Introduction
The following information explains how to solve the CVE-2007-1860 iso. It's a free pentesterlab exercise.
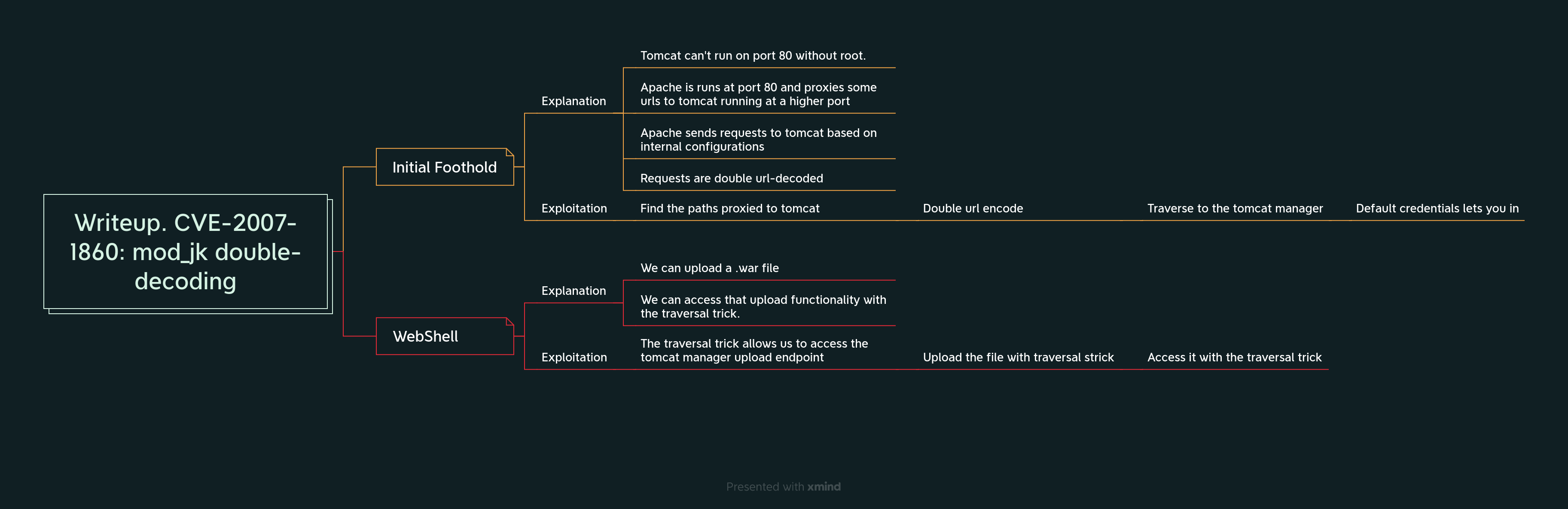
The problem with tomcat
Linux/Unix systems cannot execute tomcat on port 80 without root permissions. Tomcat does not drop privilleges at startup. For tomcat to be available for most users, it needs to execute on port 80 or 443 for https. This leads to a possible solution.
Proxying from apache to tomcat
To make the tomcat instance available for most users, an apache instance executes on port 80 and proxies the traffic to tomcat running at a higher port.
These two instances can execute on the same server or not.
The apache instance decides if the request should be proxied to tomcat or not.
It's important to figure out which instance handles the HTTP request url. You can discover this by forcing 404 pages. If the 404 page belongs to apache, the component is apache. If it's a tomcat 404 page, the component is tomcat
The problem of proxying from apache to tomcat
Both web-servers url-decode the path provided by the user. If you send %252e as input, the apache server will decode it to %2e. If the url accessed is configured to be proxied to tomcat, tomcat receives the request and url-decodes the %2e to ..
With this information, we can access the tomcat manager.
PoC
- Find a tomcat 404 page.
- Use that page to send a request to tomcat that traverses to the manager.
The tomcat 404 page can be found at: /examples/jsp/.
The payload is: https://vulnerable_host.com/examples/jsp/%252e%252e/%252e%252e/manager/html
This http request forces the tomcat manager to traverse to manager/html. (Tomcat receives the request as %2e and decodes it to . before processing it).
In we go
This instance of tomcat uses the default credentials admin:. We can base64 encode this and send it as input through the <Authorization: Basic> HTTP header.
Authorization: Basic YWRtaW46
The webshell
We can upload a .war file through the manager. There's a war webshell in github.
We need to double-encode .. again or we get a 404 page.
PoC
Ensure the authorization header is set when issuing the requests
- Download the
warwebshell from github - Set intercept to on and deploy the
warfile. In BurpSuite, insert the following contents at the beggining of the path:/examples/jsp/%252e%252e/%252e%252e(Should look like this:/examples/jsp/%252e%252e/%252e%252e/manager/html/upload) - Access the webshell with the traversal trick:
/examples/jsp/%252e%252e/%252e%252e/<webshell filename>
Conclusion
- Double URL encoding can bypass restrictions if the payload is decoded twice (or recursively).
Concise Mindmap